Deploying the Nanitor Agent with Microsoft Intune; A Step-by-Step Guide
Background
This guide provides a step-by-step approach to deploying the Nanitor CTEM Agent to Windows devices within a Microsoft Intune tenant. Previously, we showcased how to do this via Datto RMM.
Intune offers several methods for application deployment:
Intune Apps: This method involves packaging applications into the intunewin format, which requires repackaging for every update.Intune Scripts: This approach uses PowerShell scripts and Entra security group assignments for deployment.
We recommend the script-based method due to its ease of maintenance and flexibility in assigning deployments to different organizations. This guide will walk you through creating and deploying a PowerShell script to install the Nanitor CTEM agent.
Preparing Nanitor
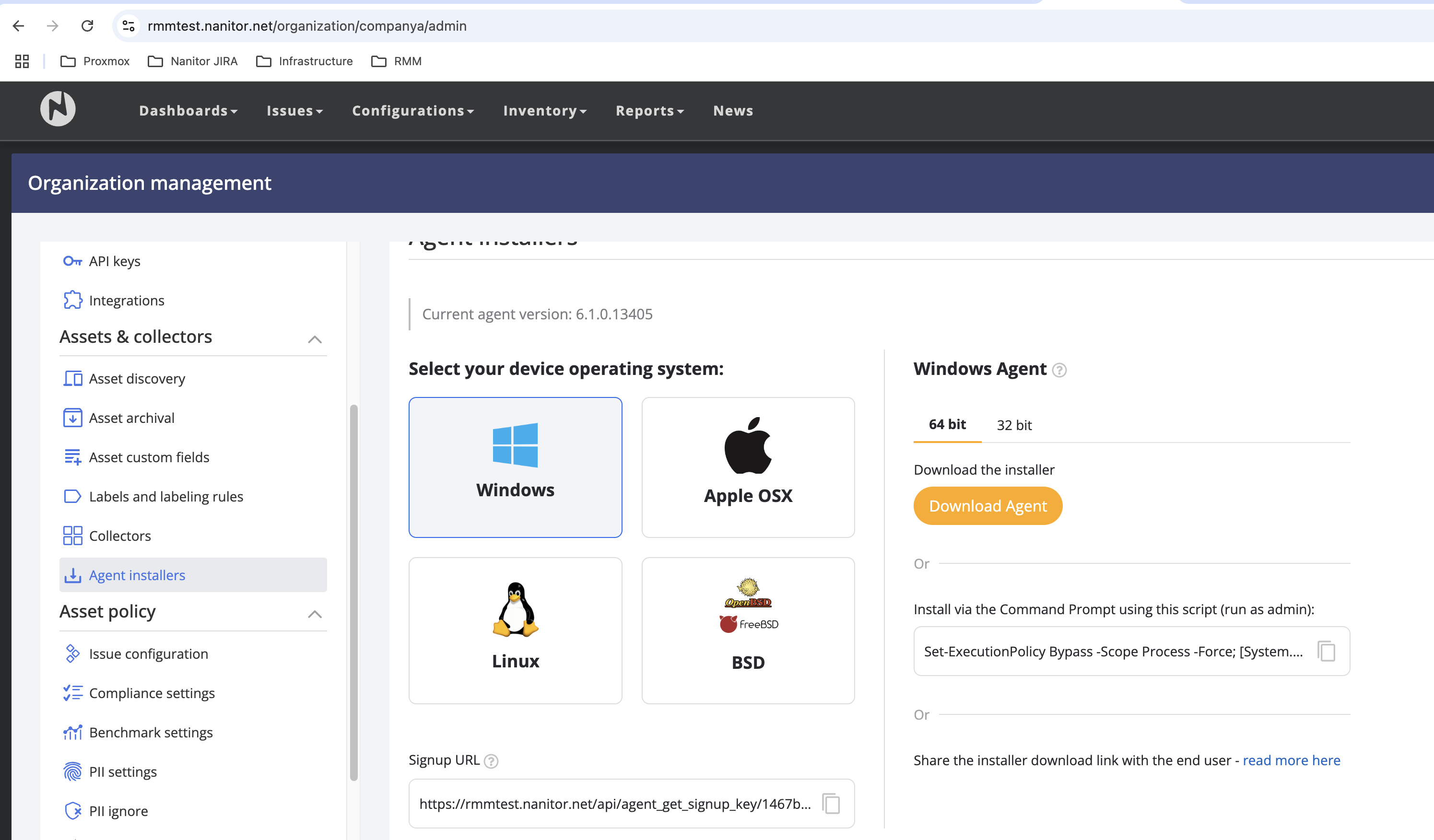
This guide assumes you have an operational Nanitor CTEM server, using the URL https://rmmtest.nanitor.net as an MSSP instance. In this setup, rmmtest serves as the top-level organization, acting as the parent organization for your customers.
For our example, CompanyA is established as an organization with rmmtest as its parent. We will deploy an Intune script to enroll the Nanitor Agent into the CompanyA organization and assign it to a test group.
This deployment strategy involves creating a unique script for each Nanitor organization and assigning it to a corresponding Entra group, providing flexibility for various needs.
To begin, navigate to the CompanyA admin page and copy the Signup URL. Store this URL securely; it will resemble https://rmmtest.nanitor.net/api/agent_signup_key/...
Nanitor Intune Script Deployment
Since this script installs the Nanitor CTEM Agent into the rmmtest.nanitor.net tenant and the CompanyA organization, we will name the script nanitor-agent-install-intune-rmmtest-companya.ps1 and include the following content:
<# Nanitor Agent installer for inTune :: build 6, march 2025
script variables: nanitorSignupURL/str
Deploy this script as an inTune script and change the $nanitorSignupURL beforehand.
#>
# Change this to reflect your Nanitor signup URL.
$nanitorSignupURL = "https://changeme/.../"
### DO not change naything beneath this line.
$INSTALLER_DIR = "${env:TEMP}\nanitor-installer"
Write-Host "Nanitor CTEM Agent Installer for inTune"
Write-Host "- InstallerDir: $INSTALLER_DIR"
Write-Host "====================================================="
# Remove the existing installer directory if it exists
if (Test-Path $INSTALLER_DIR) {
Remove-Item -Recurse -Force $INSTALLER_DIR
}
# Create the installer directory
New-Item -ItemType Directory -Force -Path $INSTALLER_DIR
# Change the working directory to the installer directory
Set-Location $INSTALLER_DIR
Start-Transcript -Path "$INSTALLER_DIR\install-intune.log"
#region Ensure Nanitor is not already present -----------------------------------------------------------------
Write-Host "- Checking if Nanitor CTEM Agent is already installed..."
if (Test-Path 'C:\ProgramData\Nanitor\Nanitor Agent\nanitor.db') {
Write-Host "! NOTICE: Nanitor CTEM Agent appears to be installed. Skipping reinstallation."
exit 0
}
#region Signup URL Checks -------------------------------------------------------------------------------------
if (!$nanitorSignupURL) {
write-host "! ERROR: No Nanitor Signup URL supplied."
write-host " The Nanitor CTEM Agent requires a Signup URL to validate installation."
write-host " Please provide it via the -nanitorSignupURL parameter."
exit 1
}
if ($nanitorSignupURL -NotLike 'https://*') {
write-host "! ERROR: Nanitor Signup URL should start with 'https://'."
exit 1
}
write-host "- Nanitor Signup URL: $nanitorSignupURL"
#region Bitness Checks ----------------------------------------------------------------------------------------
$osArchitecture = (Get-CimInstance Win32_OperatingSystem).OSArchitecture
$procArchitecture = (Get-CimInstance Win32_Processor).Architecture
Write-Host "- Detected OS Architecture: $osArchitecture"
Write-Host "- Detected Processor Architecture: $procArchitecture"
switch ($osArchitecture) {
"32-bit" {
$varArch='i386'
Write-Host "- System is 32-bit (x86)"
}
"64-bit" {
switch ($procArchitecture) {
9 {
$varArch='amd64'
Write-Host "- System is 64-bit (x86-64)"
}
12 {
Write-Host "! ERROR: Arm64 architecture detected."
Write-Host " Arm64 is not supported at this time."
exit 1
}
default {
Write-Host "! ERROR: Unknown processor architecture ($procArchitecture)"
exit 1
}
}
}
default {
Write-Host "! ERROR: Unknown OS architecture ($osArchitecture)"
exit 1
}
}
#region Download/Verify Installer -----------------------------------------------------------------------------
$downloadUrl="https://nanitor.io/agents/nanitor-agent-latest_$varArch.msi"
write-host "- Download URL: $downloadUrl"
#download......................................................................................................
[Net.ServicePointManager]::SecurityProtocol=[Enum]::ToObject([Net.SecurityProtocolType], 3072)
$script:WebClient=New-Object System.Net.WebClient
$script:webClient.UseDefaultCredentials = $true
$script:webClient.Headers.Add("X-FORMS_BASED_AUTH_ACCEPTED", "f")
$script:webClient.Headers.Add([System.Net.HttpRequestHeader]::UserAgent, 'Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.2; .NET CLR 1.0.3705;)')
$script:webClient.DownloadFile("$downloadUrl", "$INSTALLER_DIR\nanitorAgent.msi")
#verify........................................................................................................
$varChain=New-Object -TypeName System.Security.Cryptography.X509Certificates.X509Chain
try {
$varChain.Build((Get-AuthenticodeSignature -FilePath "$INSTALLER_DIR\nanitorAgent.msi").SignerCertificate) | out-null
} catch {
write-host "! ERROR: Unable to verify digital signature for Agent installer."
write-host " Please ensure your device is able to access https://nanitor.io."
exit 1
}
if (($varChain.ChainElements | % {$_.Certificate} | ? {$_.Subject -match "DigiCert Trusted G4 Code Signing RSA4096 SHA384 2021 CA1"}).Thumbprint -ne '7B0F360B775F76C94A12CA48445AA2D2A875701C') {
write-host "! ERROR: Digital signature for Agent installer did not match expected values."
write-host " Please contact Nanitor support."
exit 1
}
#region Install -----------------------------------------------------------------------------------------------
$varInstaller=Start-Process "msiexec.exe" -ArgumentList "/i `"$INSTALLER_DIR\nanitorAgent.msi`" ACCEPTEULA=yes SIGNUP_URL=$nanitorSignupURL /qn" -Wait -PassThru
switch ($varInstaller.ExitCode) {
0 {
write-host "- Installation succeeded."
} 3010 {
write-host "- Installation succeeded but a reboot is required."
} default {
write-host "! ERROR: Installation concluded with code $_."
write-host " Please check the event log to find out what the issue was."
exit 1
}
}
Make sure to change the $nanitorSignupURL variable to the signup URL we saved at the beginning of this article.
Deploying the Intune Script
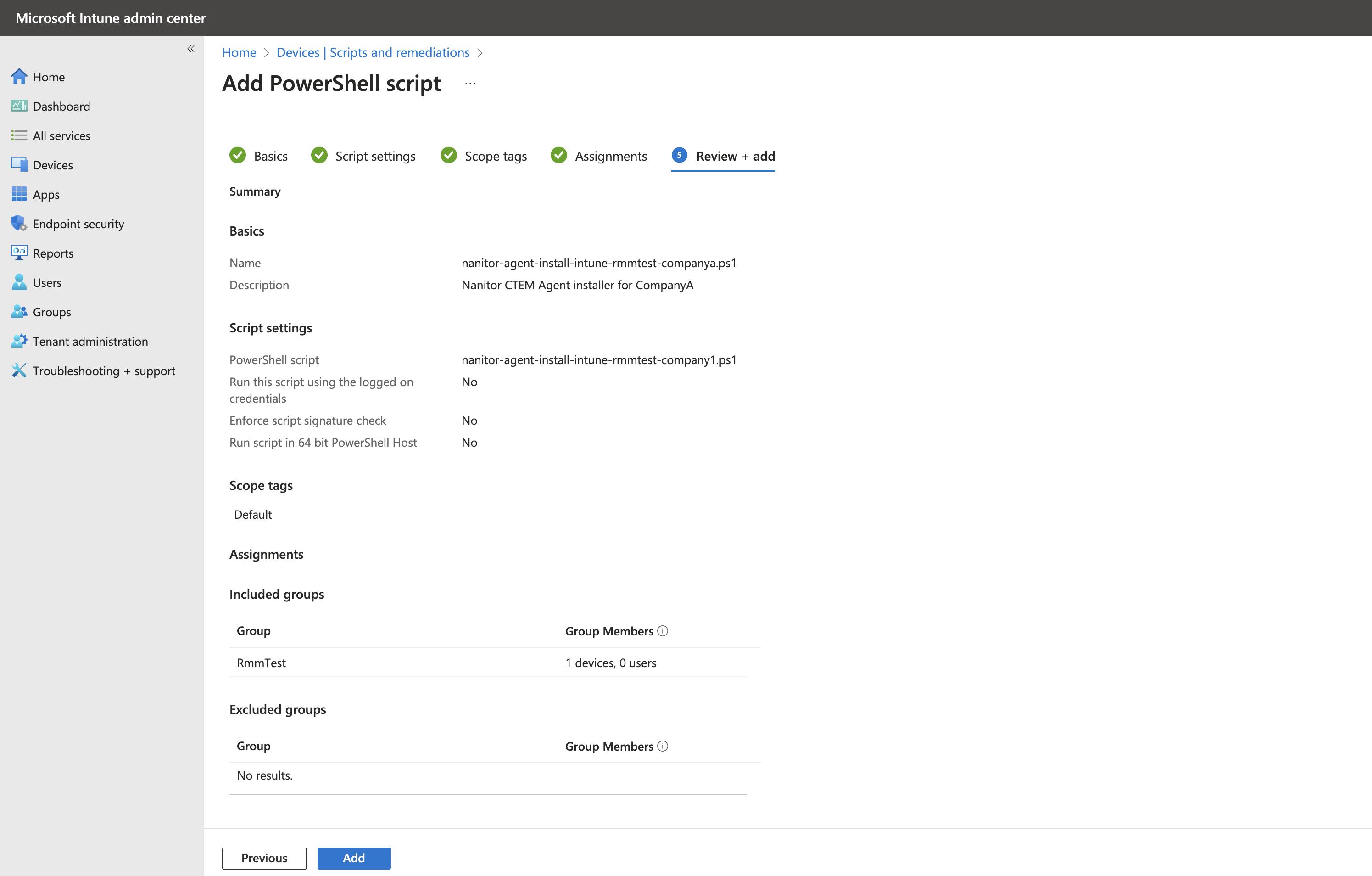
Here are the steps to deploy the Nanitor Agent installer Intune script.
- Go to the
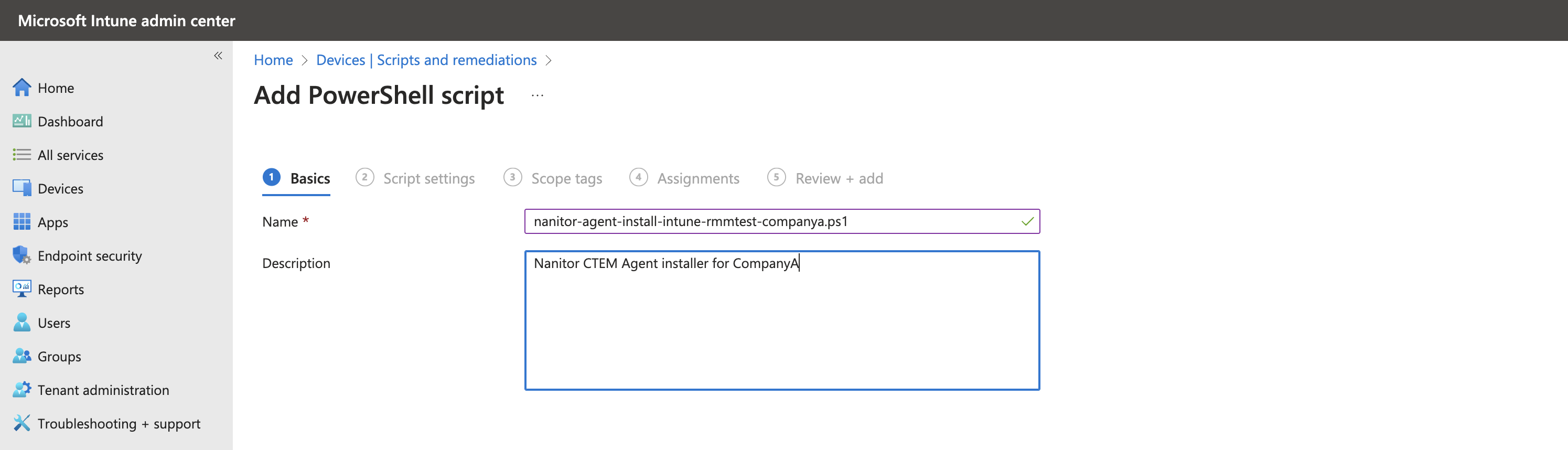
Microsoft Intune admin centerand navigate toDevices>Scripts and remediations, then select thePlatform Scriptstab. - Click Add and choose
Windows 10 and later. - Provide the following information:
Name:nanitor-agent-install-intune-rmmtest-companya.ps1Description:Nanitor CTEM Agent installer for CompanyA
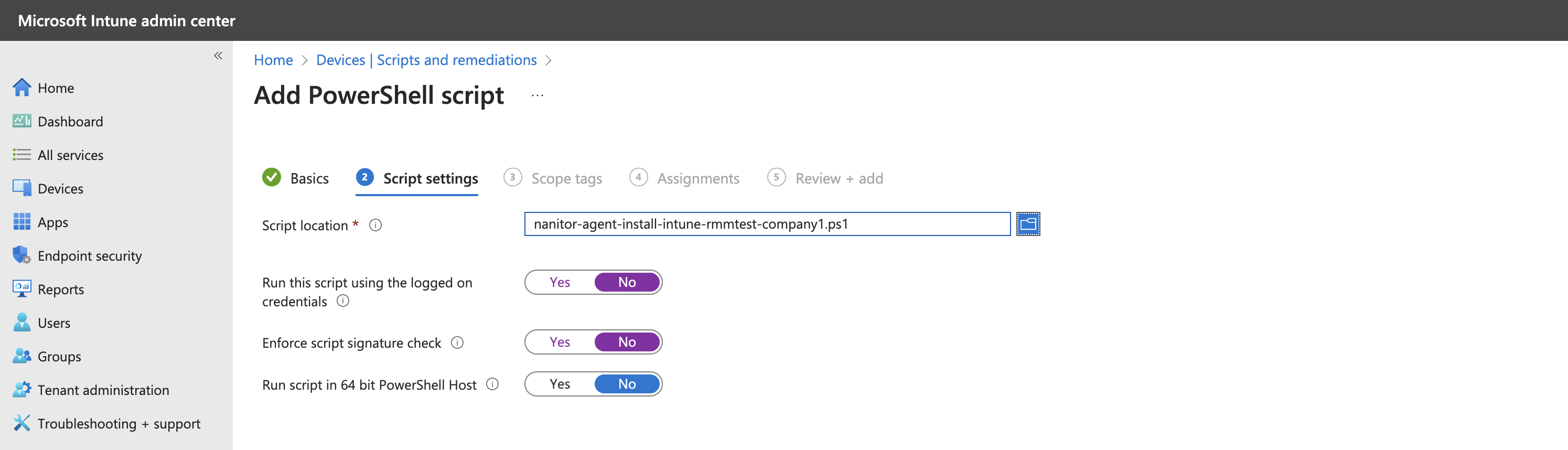
- Click Next to access the Script settings. Configure the settings as shown in the screenshot, ensuring the PowerShell script is uploaded, and the following options are set:
Run this script using the logged in credentials:NoEnforce script signature check:NoRun script in 64-bit PowerShell host:No
- Click
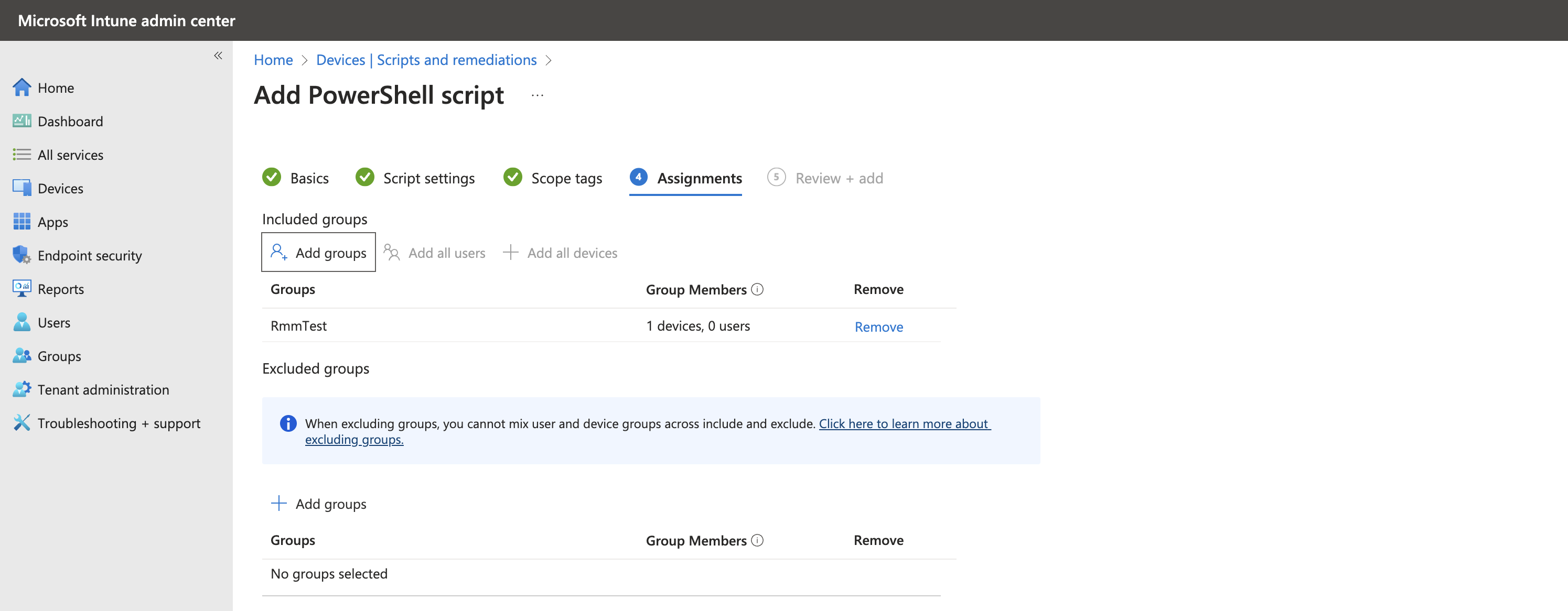
Next, bypassScope tags, and proceed toAssignments. - Assign the script to the appropriate group, which contains the devices intended for onboarding into the Nanitor
CompanyAorganization. In this case, the Intune group is namedRmmTest. - Click
Nextto review the settings. - Finally, click Add to save and deploy the script.
Results and Troubleshooting
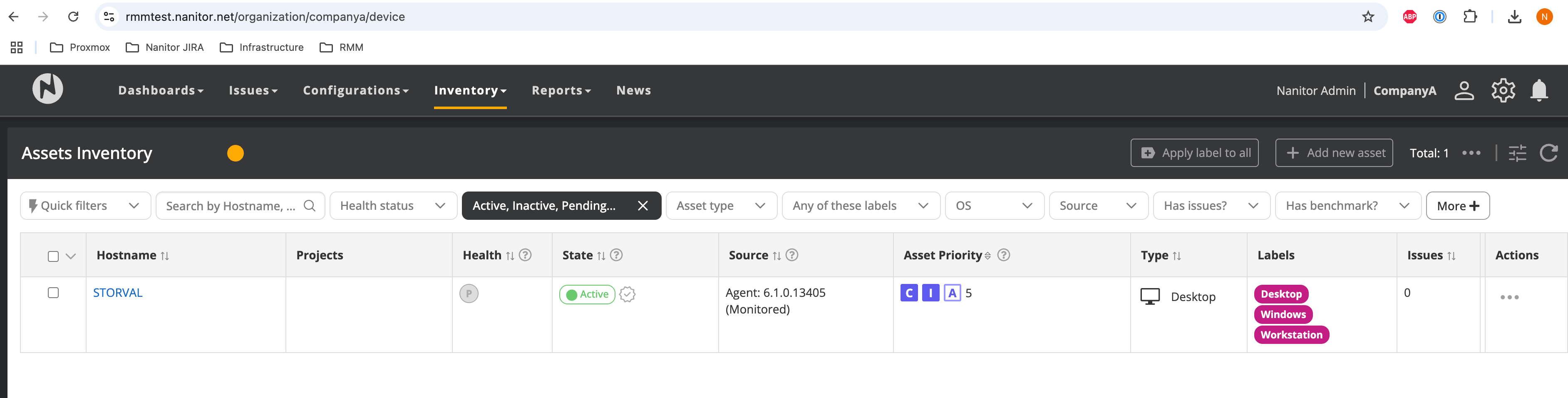
Script execution may be delayed according to the Intune schedule. To monitor the installation, check the script's log file, located at C:\Windows\Temp\nanitor-installer.
To expedite Intune synchronization, restart the Intune Management Extension service via the Task Manager Services tab. This action forces a sync and initiates script execution. In our testing, the device STORVAL appeared in the Nanitor CTEM UI within minutes of performing this action.
Conclusion
Successfully deploying the Nanitor CTEM agent via Microsoft Intune streamlines endpoint security management. By utilizing PowerShell scripts and Intune's deployment capabilities, organizations can efficiently enroll devices into Nanitor, ensuring continuous monitoring and vulnerability management. Remember to adapt the provided script with your specific Nanitor Signup URL and to consult the installation logs for troubleshooting.