Nanitor and Datto integration
Background
As CTO and head of operations at Nanitor, I enjoy prototyping new solutions. When our partner, Eyfi Stefansson at Tolvuthjonustan, approached me with an idea, I was eager to explore it. Eyfi, who has been using the Nanitor CTEM suite to monitor vulnerability threats for his customers, suggested integrating the system they use, Datto RMM, with Nanitor. He found himself frequently switching between Datto and the Nanitor portal, which was inefficient.
After some thought, Eyfi contacted me and shared his vision for the Datto RMM console. He wanted it to display the following for each managed device:
- The device's CTEM health score
- A list of critical vulnerabilities sorted by Nanitor's issue priority
- CIA Triad (Confidentiality, Integrity, Availability)
- A link to the device in the Nanitor portal
I saw this as a great challenge and, valuing our relationship with Eyfi, decided it was time to develop a prototype that could simplify his workflow. If successful, we could later explore a full Datto RMM integration. In my experience, it's always best to start with a working prototype before committing to a full integration.
Eyfi and I agreed on a collaborative approach: I would handle the Nanitor side of the integration, while he would take care of the Datto side. Once the proof of concept was complete, we'd document the process in a blog post and then decide on the next steps.
Nanitor Side
The Nanitor CTEM Agent is designed with a minimal footprint, operating on a need-to-know basis and offloading as much work as possible to the server. As a result, the agent doesn't have direct access to information like its health score or the vulnerabilities it detects. To bridge this gap, we implemented a simple API that allows the CTEM agent to retrieve this information from the Nanitor server. This enables third-party tools, such as Datto (which also has an agent on the device), to query the information in JSON format and work with it. This approach provided the simplest solution to demonstrate that the integration with Datto was feasible.
We released a beta version of this functionality to Eyfi for testing in a controlled environment.
Datto Side
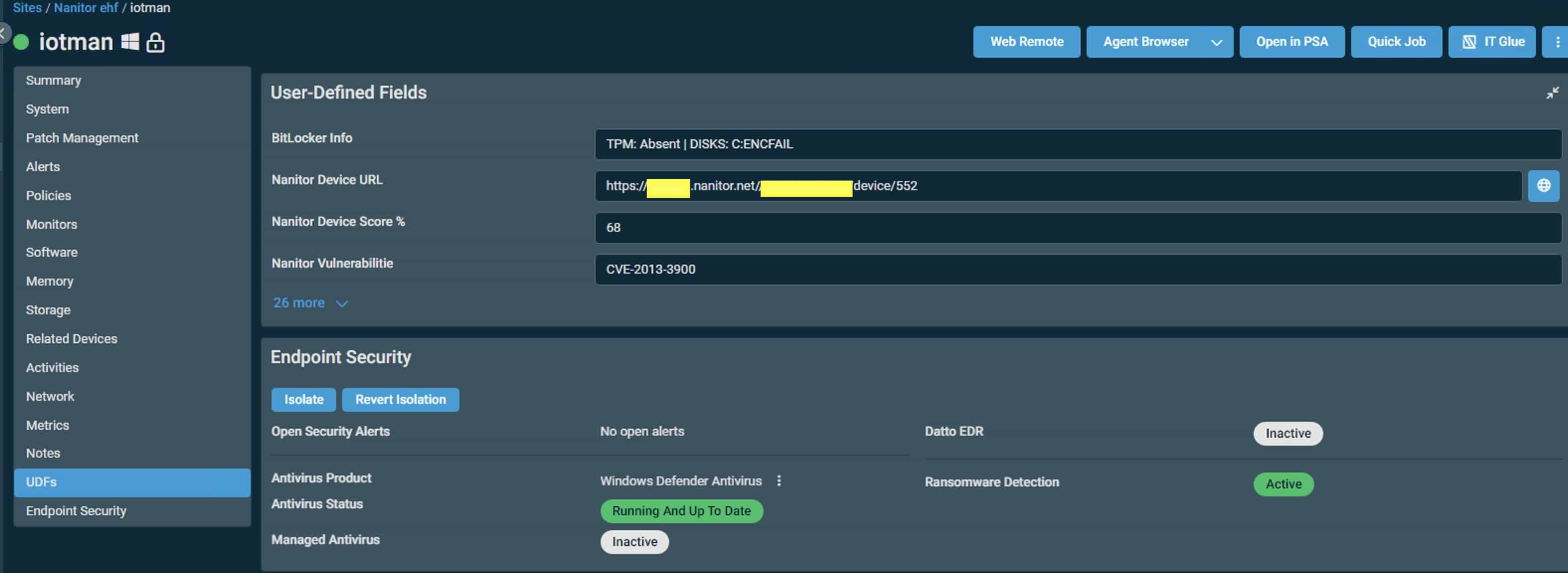
Datto RMM is an asset-centric RMM, which makes integration most effective by querying the Nanitor agent directly for device-specific information. The integration process involves creating a monitor that retrieves the JSON data from the Nanitor Agent and populates a user-defined field (UDF) in the Datto RMM console. This allows the data to be easily displayed within the Datto RMM UI.
The monitor runs on a regular basis, executing the following command: C:\Program Files\Nanitor\Nanitor Agent\nanitor-agent.exe agent_server_info. A PowerShell script then parses the output and stores the relevant information in a UDF on the Datto side.
The UI is then updated with the information from the UDF, displaying it on the detailed information page for each device.
Here is a screenshot from the Datto device page with the UDF's populated:
Conclusion and Next Steps
The proof of concept was a success, and Eyfi was able to pull all relevant information directly into the device details within Datto RMM, significantly reducing the time spent switching between platforms. He can now trigger workflows that log service desk tickets when CTEM detects vulnerabilities on devices. This also allows him to clearly demonstrate the value of the service to his customers, showing how vulnerabilities are closed within the defined SLA when systems are patched. This improves both transparency and the perceived value of the service.
There are already various feature and improvement requests from Eyfi that we're reviewing.
Eyfi remarked that we're now on a journey to fully close the gap, enabling him to offer top-tier security services to his clients. In this collaboration, Datto's role includes:
- Patching vulnerabilities
- Having the Datto SOC review security incidents
- Running security audits and penetration tests using Datto consultants, if required
Nanitor plays a crucial role in this process by:
- Continuously feeding CTEM threat intelligence into Datto
- Providing remediation instructions to patch and mitigate vulnerabilities
- Supplying relevant security data to the Datto SOC, adding critical context that Nanitor gathers from the devices and network
Our next steps are to closely monitor the progress with Eyfi while exploring deeper integration with Datto. This could reduce the amount of custom code Eyfi needs to maintain and potentially open the door to onboarding more MSPs using Datto into the Nanitor MSSP program.